
Lazarus Group Targets Crypto Exchange with Kandykorn Malware
Elastic Security Labs said on Oct. 31 that Lazarus Group attempted to hack a crypto exchange using new malware.
Elastic dubbed the new malware “Kandykorn” and the loader program that installs it into memory “Sugarload,” which has a distinctive “.sld” extension.
The targeted exchange was not named by Elastic. Most 2023 crypto exchange private-key attacks have been linked to the North Korean cybercriminal Lazarus Group.
Elastic said Lazarus members disguised as blockchain engineers attacked unnamed crypto exchange engineers. The attackers claimed on Discord that they had created a profitable arbitrage bot to profit from cryptocurrency exchange price differences.
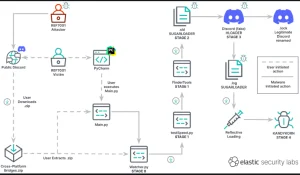
Kandykorn infection process. Source: Elastic Security Labs
The attackers got engineers to download this “bot.” The ZIP folder contained files named “config.py” and “pricetable.py” that resembled arbitrage bots.
When the engineers launched the application, it ran “Main.py,” which ran some normal programs, and “Watcher.py,” which was dangerous.
Watcher.py connected to a distant Google Drive account and downloaded content to testSpeed.py. To hide it, the malicious program executed testSpeed.py once before removing it.
The single-time execution of testSpeed.py downloaded more content and executed Elastic’s “Sugarloader.” This file was obfuscated with a “binary packer,” Elastic said, avoiding most malware detection systems.
By stopping the application after its initialization functions were called and snapshotting its virtual memory, they found it. Elastic ran VirusTotal malware detection on Sugarloader and found no malware.
After downloading Sugarloader, it linked to a remote server and downloaded Kandykorn into memory. The remote server can employ several Kandykorn functions to commit crimes.
For instance, “0xD3” lists the contents of a directory on the victim’s computer, and “resp_file_down” transfers any victim file to the attacker’s machine.
Elastic supposes the attack happened in April 2023. According to the report, the program may still be utilized for assaults, as centralized crypto exchanges and apps experienced a surge in attacks in 2023.
These attacks have targeted Alphapo, CoinsPaid, Atomic Wallet, Coinex, Stake, and others. Most involve the attacker acquiring a private key from the victim’s device and transferring the client’s cryptocurrency to their address.
The FBI has accused the Lazarus Group of hacking Coinex, Stake, and others.





