MailerLite revealed that a social engineered attack on a customer care employee who unknowingly granted access to the internal system.
Hackers were able to obtain access to the accounts of significant Web3 organizations in order to carry out phishing email scams that resulted in the loss of approximately $3.3 million from subscribers.
According to the email marketing company MailerLite, which has validated this information. Emails sent from the official accounts of WalletConnect, Token Terminal, and De.Fi contained malicious URLs that harbored wallet-draining software.
MailerLite disclosed the specifics of how a social engineering operation targeted an employee working in customer care, infiltrating its system, a few hours after the emails were sent out to subscribers.
The statement reveals that while responding to a client request through our support portal, a team member clicked on an image that misleadingly linked to a fraudulent Google sign-in page.
In the subsequent step, the employee unknowingly authenticated access, which allowed the attackers to gain access to the internal administrative panel of MailerLite.
“With this level of access, they were able to impersonate user accounts. The focus was exclusively on cryptocurrency-related accounts.”
Additionally, the hackers were able to obtain additional power by resetting the password of a particular user through the administrative panel.
According to MailerLite, the hackers gained access to 117 accounts, although they only exploited a limited number of those accounts in order to begin phishing activities.
The service provider became aware that the hackers had compromised the data of its customers and subscribers, including complete names, email addresses, and other personal information uploaded to MailerLite.
The blockchain analytics platform Nansen assisted in determining the worth of the assets stolen by the attackers. The research team has determined that the primary phishing wallet received a total of $3.3 million in inflows.
The research team determined this by tracking token flows on blockchains supported by Nansen. Xbanking tokens, on the other hand, appear to be trading exclusively on the Latoken exchange (according to CoinGecko), accounting for $2.6 million of that total.
According to Nansen’s team, “2.6 million is 80% of its full diluted valuation, and it could be difficult to convert it.” Nansen’s team concluded.
Nansen narrowed down the amount of stolen funds, which are more easily convertible to be worth $700,000, by subtracting the Xbanking (XB) tokens from the total number of monies taken.
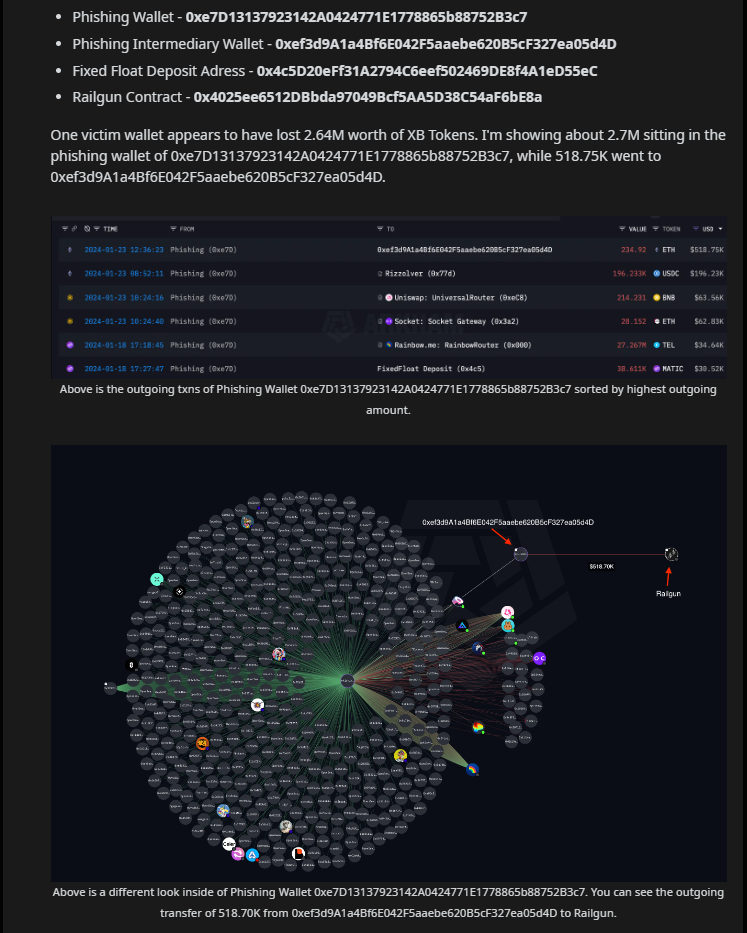
An anonymous user on Reddit also arrived at a similar estimate of the total amount of money stolen as a result of the incident. Nansen provided evidence that supported the conclusions, which included a reference to XB tokens.
Nansen and Reddit both brought attention to the fact that the perpetrators of the hack utilized the privacy protocol Railgun in order to conceal the transfer of stolen tokens.
The system utilizes zero-knowledge cryptography and is a privacy solution built directly on-chain for Ethereum, BNB Chain, Polygon, and Arbitrum. Its purpose is to enable the private use of smart contracts and decentralized finance protocols.












